Known Plaintext attack vs Chosen plaintext attack - Blog on Information Security and other technical topics
GitHub - drBearcub/-ciphertext-only-attack: Java Implementation of ciphertext-only cryptanalytic for cryptography class
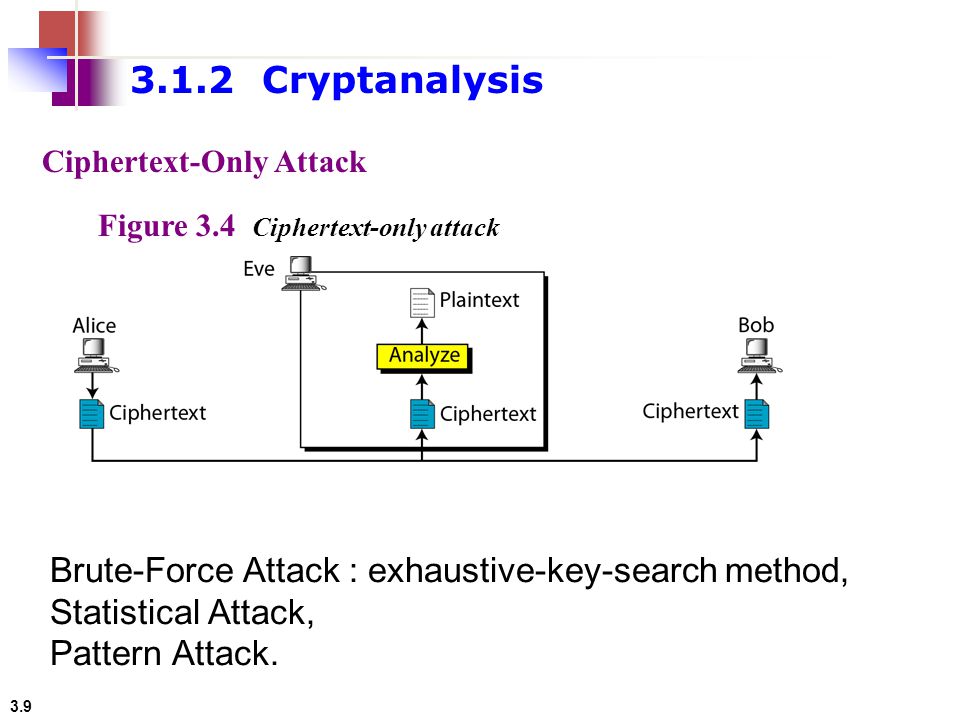
3.1 Copyright © The McGraw-Hill Companies, Inc. Permission required for reproduction or display. Chapter 3 Traditional Symmetric-Key Ciphers. - ppt download
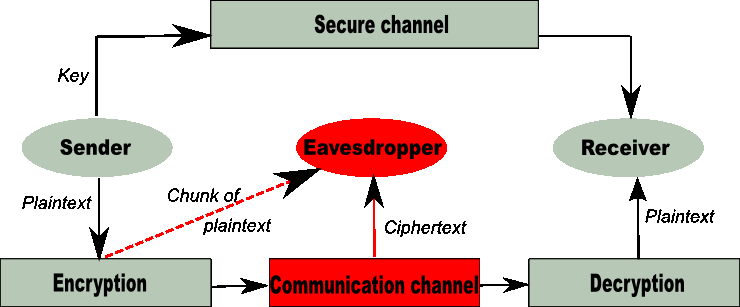
Basic Concepts in secure communication ❑ The security of the communication depends on the security of the key. It must be conv